@JosephWhite, any insight: I have the answer and it matches the hinted characters, but it’s not accepting my answer. Thanks!
i am having same problems too
Could you please elaborate on exactly which problem you’re encountering here? Exact Lesson and Step number - plus a screenshot. Thanks!
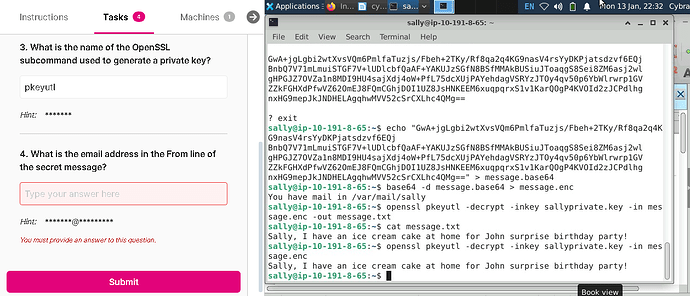
It appears that you are typing in the syntax descriptions as actual commands.
For example, at Part 2, Step 2, we explain the parts of the command that will be used in the next step as “openssl pkeyutl -encrypt -inkey [public].key -pubin -in [filename].txt -out [filename].enc” where the bracketed terms are placeholders for that actual parameters we are using in the lab environment.
Said differently, don’t type “openssl pkeyutl -encrypt -inkey [public].key -pubin -in [filename].txt -out [filename].enc”
Just type “openssl pkeyutl -encrypt -inkey Downloads/sallypublic.key -pubin -in message.txt -out message.enc”
someone help !! answer for question 4 !!
You see who the email to sally is From: when you open email 1 in step 3.
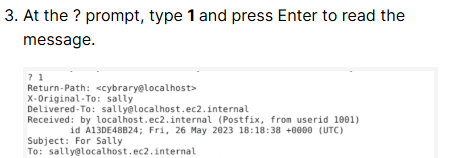
[redacted]@localhost
is not the right answer for me!!
[image removed]
[image removed]
sallyprivate.key is not the right answer for me !!!
pkeyutl is not used to create a private key. You use the correct tool in Step 1.
sallyprivate.key is not used to encrypt a message for user cybrary. In the lab cybrary used sallypublic.key to encrypt a message, and sally used sallyprivate.key to decrypt. So what key would be needed for sally to encrypt a message for cybrary?
From the Core Concepts…
"Overview
There are two types of cryptographic algorithms: symmetric and asymmetric. Asymmetric cryptography (also known as public key cryptography) uses two mathematically-related cryptographic keys to encrypt plaintext and decrypt ciphertext: a public key and a private key. As the name implies, the public key can be widely distributed and used to encrypt messages. Those encrypted messages can only be decrypted using the private key, which is never distributed beyond the key owner, and ensures the confidentiality of any messages sent to the key owner."
So, if we read that carefully we see the public keys are used to encrypt, and private keys are used to decrypt. So if user sally want to encrypt a message to user cybrary she will need whose public key?
When attempting the following, pkeyutl is not found. I tried using “locate” and the “find” commands and pkeyutl is nowhere to be found. Can anyone help please ?
openssl pkeyutl -encrypt -inkey Downloads/sallypublic.key -pubin -in message.txt -out message.enc
Are you sure you’re entering the command correctly, and completed all previous steps in the lab? I just tested the lab and it seems to be working fine.
Thank you, it appears to be working today though I cannot spot where my syntax was different from what you showed in your screenshot. Regardless, thanks much ![]()