I tried everything and still not getting right. Any help would be appreciated-
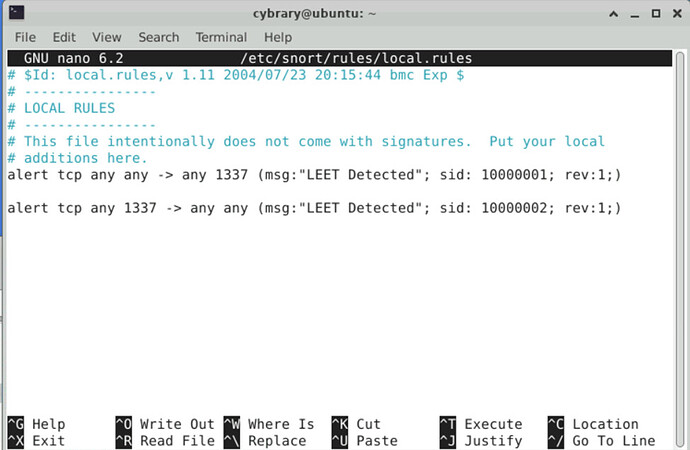
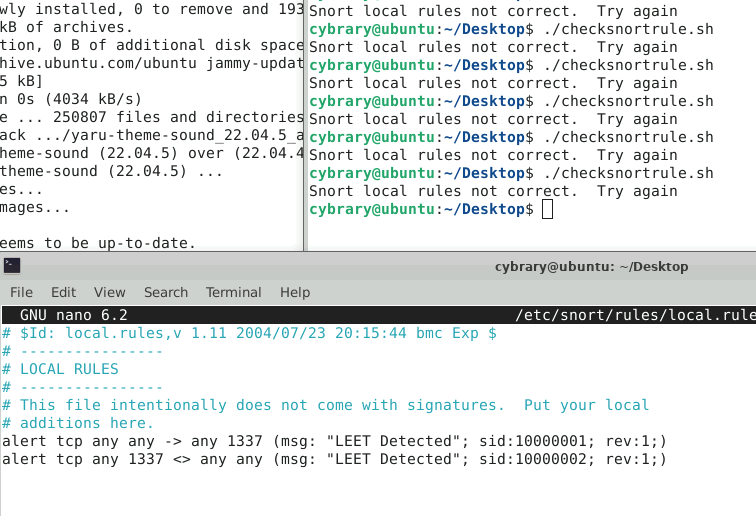
After running the .sh file, it says that the First rule is right. Is there something wrong in 2nd rule?
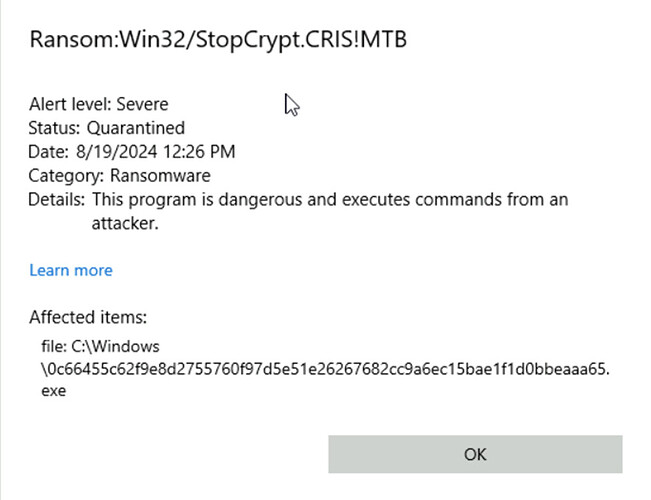
This is what Windows Defender shows after I extract Sample2 file and place the malware in Windows Folder. The placeholder given under the question was different from what is shown above in the image.
Thanks in advance
1 Like
On the second rule, try “<>” instead of “->”. For the defender question, I think Microsoft has changed how they classify Sample2. Try Win32/Andromeda!ic
1 Like
Thanks a lot. This worked 
yes new version is Ransom:Win32/StopCrypt.CRIS!MTB
I am having this same issue today. I have setup the snort rules that I think should be accepted but the flag will not be provided.
I have set:
Are either of these incorrect? I changed rule 2 to match the guidance given above but → is also not accepted.
Try removing the space between msg: and “LEET Detected”
alert tcp any any → any 1337 (msg:“LEET Detected” …
It may be a grader thing.