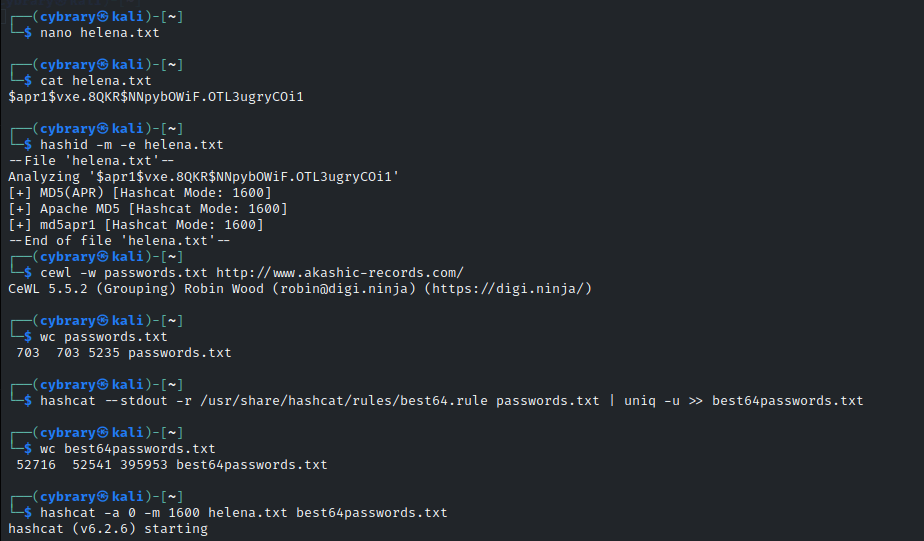
I am having trouble completing this lab on Password Cracking Challenge Exercise 1.3 since it seems to be the file is not correct or the instructions are not correct. I had followed the procedure as follows:
- Recon: wget -O htpasswd.txt http://psybrary.com/.htpasswd
- examine file: cat htpasswd.txt
- the file shown the username: hash
- idenfied the hash: hashid -m -e I had copied the hash only placed hereinstead of the <>.
- created a custom wordlist: cewl -w custom.txt http://psybrary.com/OurInspirations
- I had cat the custom.txt file and it was good.
- prepare the Attack Wordlist with the best64.rule: hashcat --stdout -r /usr/share/hashcat/rules/best64.rule custom.txt | uniq -u > new_wordlist.txt
8.Cracking the password hash: hashcat -a 0 -m 1600 (this mode was selected since the hash had shown to be for an Apache MD5) htpasswd.txt new_wordlist.txt - The process completed successfuly but couldnt crack the password hash.
Has any one ran into this issue or is my procedure incorrect?