Hello Dear Colleagues.
I have exhausted myself trying to figure our second flag… have ssh connected on C2-1 and C2-2 (prove: when i curl 127.0.0.1:8888 it responses with(<p>HELLOW WORDL</p>), and started a http.server listen on my machine, but when I try to ping from either C2 hosts, it says can’t reach…
Could you guys help me with it? what else should be done after reaching C2-2 to have the flag
Hey there - I’ve shared a bit of the instructor’s solution guide below.
The second endpoint (router) 192.168.100.254 has a single port 8000, which shows up as OpenSSH when nmap’s service and version scanning scripts are used. When attempting to login, it’s evident that its C2-2’s ssh port.
Next, you will need to issue a command that can “connect” the two services together - ie brokering access between the C2-2 host (listening on 127.0.0.1:8888) and an automated service on the compromised host that makes HTTP calls on 127.0.0.1:8888.
Thanks for help. It was quite a challenge for me… I was able to solve it at last but need to deepen my knowledge in this field.
Glad to hear it! I agree that this one is quite hard, relative to the Learn material and other Challenges. Well done on pushing through it.
I am doing this challenge now as well and I cannot figure out how to even get started on flag 1, any tips?
Here’s a bit more of the instructor’s solution guide, edited down to not give too much away:
The scenario starts on an Ubuntu desktop with a memo containing information about how to complete the challenge, as well as an encrypted file containing the final flag.
You’ll want to begin by scanning the Web Proxy and Firewall hosts.
One of those hosts should have a single open port, with your nmap scan revealing some information about proxy services.
Test this by making proxy calls through that proxy and to the internet or any other site. If you use the correct OpenSSH / ProxyCommand one-liner, you should be able to access the C2-1 host.
Once you have gained access to C2-1, execute cat /flag.txt to access the flag.
The second endpoint has a single port that shows up as a particular service when nmap’s service and version scanning scripts are used.
By using the correct command you can “connect” the two services together:
Once the two services are connected, the encrypted flag file on the desktop will automatically decrypt.
I am using the nc command to connect the proxy and firewall and I get a response that just says SSH-2.0-OpenSSH_9.7, then noting happens
Am I on the right track?
The instructor is expecting an ssh command. I would review the Tunneling and Pivoting lab to refresh yourself on the switches that are expected - specifically the Guided Exercise, Part 2: Tunneling and Pivoting with SSH Dynamic Port Forwarding.
I’ve included the full command from the solution guide below, with the exact characters edited out.
ssh -* -* -* ****:***.*.*.*:**** *******@***.***.***.*** -p ****
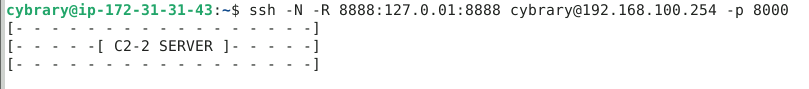
I did this command and I waited a few times and nothing happened ![]()