Hi,
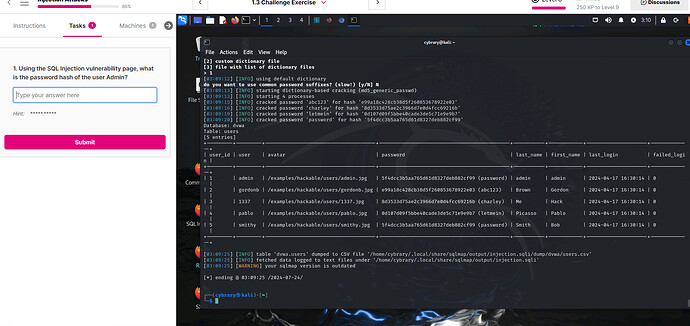
In the final task of injection attack " Using the SQL Injection vulnerability page, what is the password hash of the user Admin?" …the hash does not exists in the shawdow file nor the user in sql injection site has access to the shadow file?
I’ve also noticed this
So i think this is an issue with the lab
I got to the hashed value, and its for the encryption its md5 but nowhere near the answer it’s asking for
I don’t know what it’s asking for:
Technically, even with SQL map, we have the password right here, and it’s cracked, or we hash cracking site, and it’s here. Is it not referring to SQL? I am more than lost on this one.
I think you folks are right and there is a bug here. I will surface this to Cybrary.
So the question you saw before was not correct. There are supposed to be 4 questions. This has been resolved. Also you will find you can now answer the first question based on the findings from SQL Map.
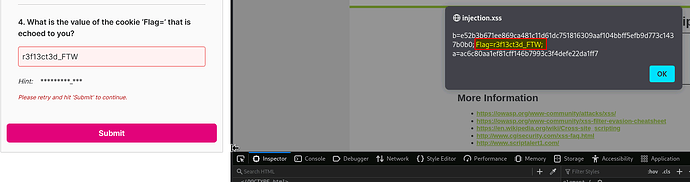
I was also running into bugs when performing this lab, I’m not sure how many times I retyped this to make sure I wasn’t making input errors
There was a “l” in the answer key instead of a “1” … this has been fixed. Your answer should work now.
I thought that, but the wording was a bit off. That was my confusion.
I think I focused too much on cracking the admin password.
Same issue, the lab developer misspelled the answer file. Your answer will work now.
Cybrary should send you a t-shirt for your QA work ![]()
hahahahahahahahahahaha I’ll happily take one
Or if they want one a QA tester! lol
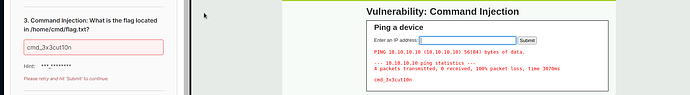
Sadly, that has not been updated, though. I even checked the home /home/cmd folder, It’s the same issue, but that answer is correct; it might not have been synced just yet. But hey, at least I know that’s the answer.
I submitted another ticket