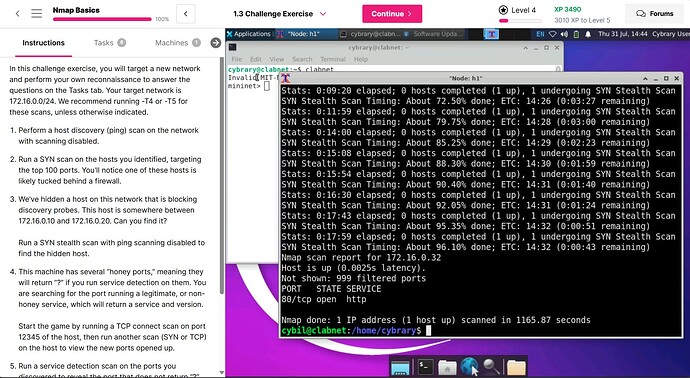
In this challenge part 1.2 of NMap Basics, we are provided with two host on network: 172.16.0.0/24. Which are: 172.16.0.32 and 172.16.0.254, and we are aimed to find a host using firewall. So basically, I used SYN scan on both the host with both T1 and T5 time, but not able to find which one is using firewall. The basic idea is to scan top 100 port on both the port and to find any port which filtered and break 3-handshake rule.
How to solve this.
Some time ago I completed this lab and I had no problem ![]()
By the way, the title says 1.2 and the challenges are 1.3. Your question is about 1.3?
Let me see in my notes and I’ll try to give you some tips ![]()
That’s it, some activities you should use “sudo” and others you shouldn’t ![]()
I hope this helps you ![]()
Ohh, I mean to say part 2 of 1.3 challenge. I did tried several scan with variations for each host, could able to find some open ports, but not able to find any thing which could suggest that a host is hidden behind firewall.
The instructions can be a bit confusing. There are three systems to discover.
In Steps 1-2 you discover two hosts. First you do a ping scan to discover the hosts, then a SYN scan. When you do the SYN scan is when you will see that one host responds and the other acts like there are no open ports. THAT host is “the host behind the firewall”.
Then in Steps 3-5 you are dealing with ANOTHER host that does not respond to ping scans and this is why you do not see it in Steps 1-2. Follow Steps 3-5 to enumerate this THIRD host.
Finally, in STEP 6, we RETURN to the “host behind the firewall” you discover in Steps 1-2. You will need to use a very slow TCP Connect scan to enumerate this host.
The trick is in some parts to use:
sudo + command + parameters
and in other cases to avoid sudo ![]()